Let’s take a closer look at the issue because in some situations, this one included, ignorance is most definitely NOT bliss.
Antiviral Factory 2013 can be very dangerous and if you’re not completely sure what you’re looking for if you wish to install security software on your PC or laptop, you may well end up downloading and paying for something that is either useless – or worse – malicious. And even more galling is the thought that you’ve been conned and are merely being used to line the pockets of unscrupulous cyber criminals.
As more and more of us are getting more computer savvy it is easy to fall into the trap of thinking that we know what we’re doing online and what we’re downloading but that may not be the case.
Antiviral Factory 2013 works by convincing you that your computer is riddled with viruses and that it has lots of different forms of malware or unwanted software installed on it.
It usually finds its way on to your machine either after you have unwittingly visited a malicious web site or it will exploit some vulnerable lapse in your PC’s existing security. You will then see a pop up window which will normally look very professional or will have even been designed to emulate a reputable anti-virus software brand. The pop up box will ask you if you want to run a scan on your computer and guess what happens if you click ‘yes’? After pretending to have scanned your machine the fake software will return results telling you that you have dozens of potentially very dangerous issues on your system. Now that’s a surprise!
You are probably already one step ahead of me at this point and have already guessed that if you want the software to ‘remedy the problem’ you will need to pay for it. Not only will entering your credit card details into the software’s system mean that you are in effect paying for absolutely nothing, but you’re also handing over sensitive information to people whose aim is to extort money out of innocent web users. Antiviral Factory 2013 isn’t cheap either; often retailing for somewhere in the region of $50 to $100 per time. But when you’re faced with a realistic looking warning from what you believe to be a computer program that is trying to help you, and you believe that your online security, files, documents and data are at risk, doesn’t it seem so much easier just to get rid of the threat there and then by clicking the ‘pay now’ button.
In order to get rid of Antiviral Factory 2013 malware, please follow the removal instructions below. Even though you can remove the core files of this malware manually, I highly recommend you scanning the system with anti-malware software. Very often, this rogue security program comes bundled with Trojans and rootkits. If you won't remove these, you may end up with even worse situation than this. If you have any questions or suggestions, please leave a comment below. Your thoughts are always welcome. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: Antiviral Factory 2013 removal guide using activation key:
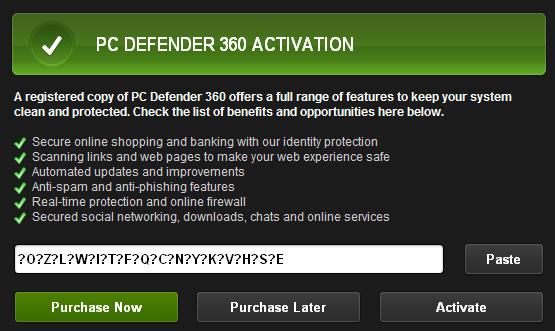
1. Open Antiviral Factory 2013. Click the "Registration" button.
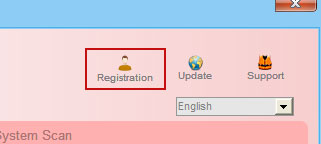
Enter the Antiviral Factory 2013 activation key given below and click "Activate" to activate the rogue antivirus program. Don't worry, this is completely legal since it's not genuine software.
AA39754E-715219CE
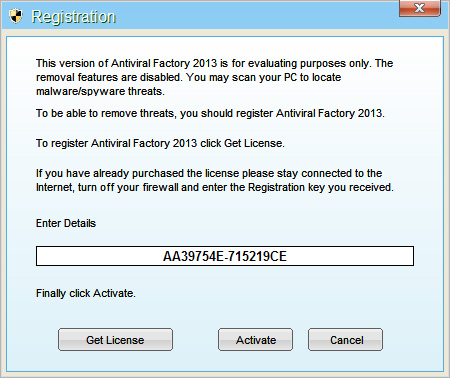
Once this is done, you are free to install recommended anti-malware software and remove Antiviral Factory 2013 malware from your computer.
2. Download recommended anti-malware software (direct download) and run a full system scan to remove this malware from your computer.
NOTE: if you can't run anti-malware software, rename the installer to winlogon.exe and try again.
Method 2: Antiviral Factory 2013 removal in Safe Mode with Networking:
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software (direct download) and run a full system scan to remove this malware from your computer.
NOTE: if you can't run anti-malware software, rename the installer to iexplore.exe and try again.
Method 3: Antiviral Factory 2013 manual removal guide:
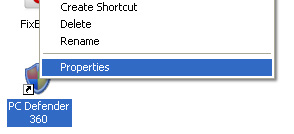
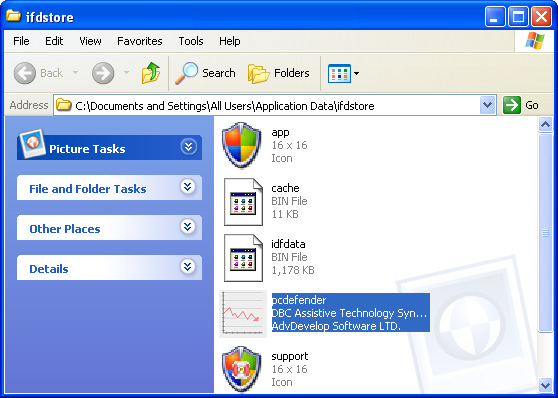
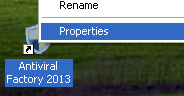
1. First of all, go to your Desktop and right click the Antiviral Factory 2013.lnk shortcut file and select Properties.
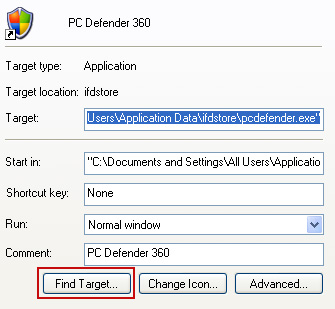
2. Select Shortcut tab. Find the location of Antiviral Factory 2013 executable file (target location). It should be a randomly named file. Simply click the Find Target button.
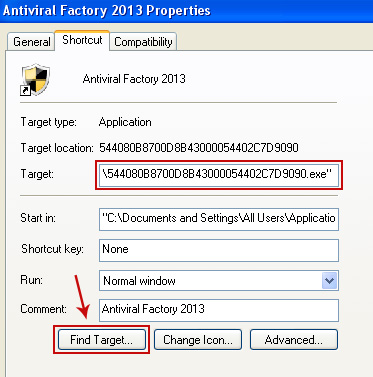
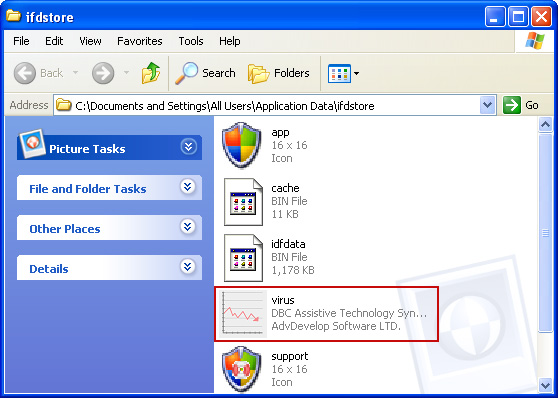
3. Browser to the executable file. Rename it, for instance to virus.exe. Restart Windows.
4. Download recommended anti-malware software (direct download) and run a full system scan to remove this malware from your computer.
NOTE: if you can't run anti-malware software, rename the installer to winlogon.exe and try again.